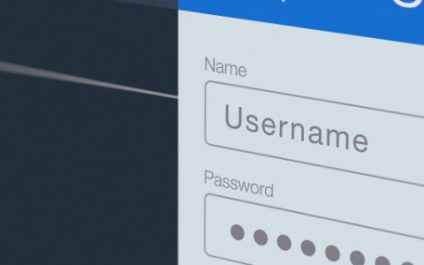
For small or medium-sized businesses (SMBs), cybersecurity often feels like an arms race. Every year, new threats emerge, forcing SMBs to revise their digital defenses. Now, password managers are in the crosshairs. A recent study reveals a staggering increase in malware targeting password managers, marking a significant shift in cyberattack strategy. The rising threat of […]
Attacks targeting password managers triple: A wake-up call for SMBs
Retailers: Don’t let the Grinch steal your cheer (and your customer data)

The holiday season is exciting for retailers, bringing a surge in customers and sales. However, with this increase comes a heightened risk of cyberattacks. Hackers know that businesses are busy and distracted during this time, making it the ideal moment to strike. From ransomware to phishing schemes, cybercriminals have a range of tactics to exploit […]
Keep your business safe from common cyberthreats

Cyberattacks pose a significant threat to businesses of all sizes, from small businesses to huge corporations. No company is immune. Therefore, you need to learn about common cyberthreats and how to prevent them so that you can better protect your business, employees, and customers. Malware Malware refers to any malicious software designed to steal data, […]
Mac malware 101: From prevention to protection

For years, Macs have enjoyed a reputation of being invulnerable to malware attacks. While the inherent security features of macOS offer a head start, complacency can be a dangerous enemy. Even Macs can fall prey to malicious software, posing a significant threat to your business data, employee privacy, and operational continuity. This article will provide […]
Must-know cybersecurity terminology to keep your business safe

Cyberthreats are constantly evolving, and without adequate protection, businesses can fall victim to data breaches, financial losses, and reputational damage. Understanding basic cybersecurity terms is crucial for safeguarding company assets and sensitive information. Here are some essential cybersecurity terms that every business owner should be familiar with to strengthen their organization’s security posture. Malware Malware […]
The stealthy intruder: Understanding fileless malware

In recent years, the cybersecurity landscape has witnessed a rapid evolution of malicious tactics, and fileless malware has emerged as a prominent weapon in the arsenal of cybercriminals. By leveraging legitimate tools and processes present on targeted systems, fileless malware bypasses traditional security measures, leaving security professionals scrambling to find effective countermeasures. This article will […]
Beware: Macs aren’t immune to malware

Macs are known to be pretty secure as they don’t seem to get viruses and malware as easily as Windows computers do. But the truth is, no computer is completely immune to malicious software. So how can you tell if your Mac has been infected with malware? Look out for these signs. Types of malware […]
Keeping PHI safe from cybercriminals
Most commonly used terms in cybersecurity explained

With so many different IT security terms and concepts that you need to learn when running a business, where should you start? Diving into cybersecurity can be challenging, but learning about the most commonly used terms in IT security is a good place to start. Understand these basic terms so you’ll be better prepared to […]
Thinking of jailbreaking your iPad? Think again

If you’re looking for ways to install unofficial apps on your iPad or change its default operating system, then you’ve probably heard of jailbreaking. But before you have your device jailbroken, here are some important facts you need to know. What is jailbreaking? Jailbreaking or rooting is the process of removing manufacturer and/or carrier restrictions […]